部署EKS集群并初始化
1.基础介绍
Amazon EKS 是一项托管服务,借助该服务,您可以轻松在 AWS 上运行 Kubernetes,而无需安装和操作您自己的 Kubernetes 控制平面.
2.创建EKS集群
2.1 AWS-WEB页面创建EKS集群
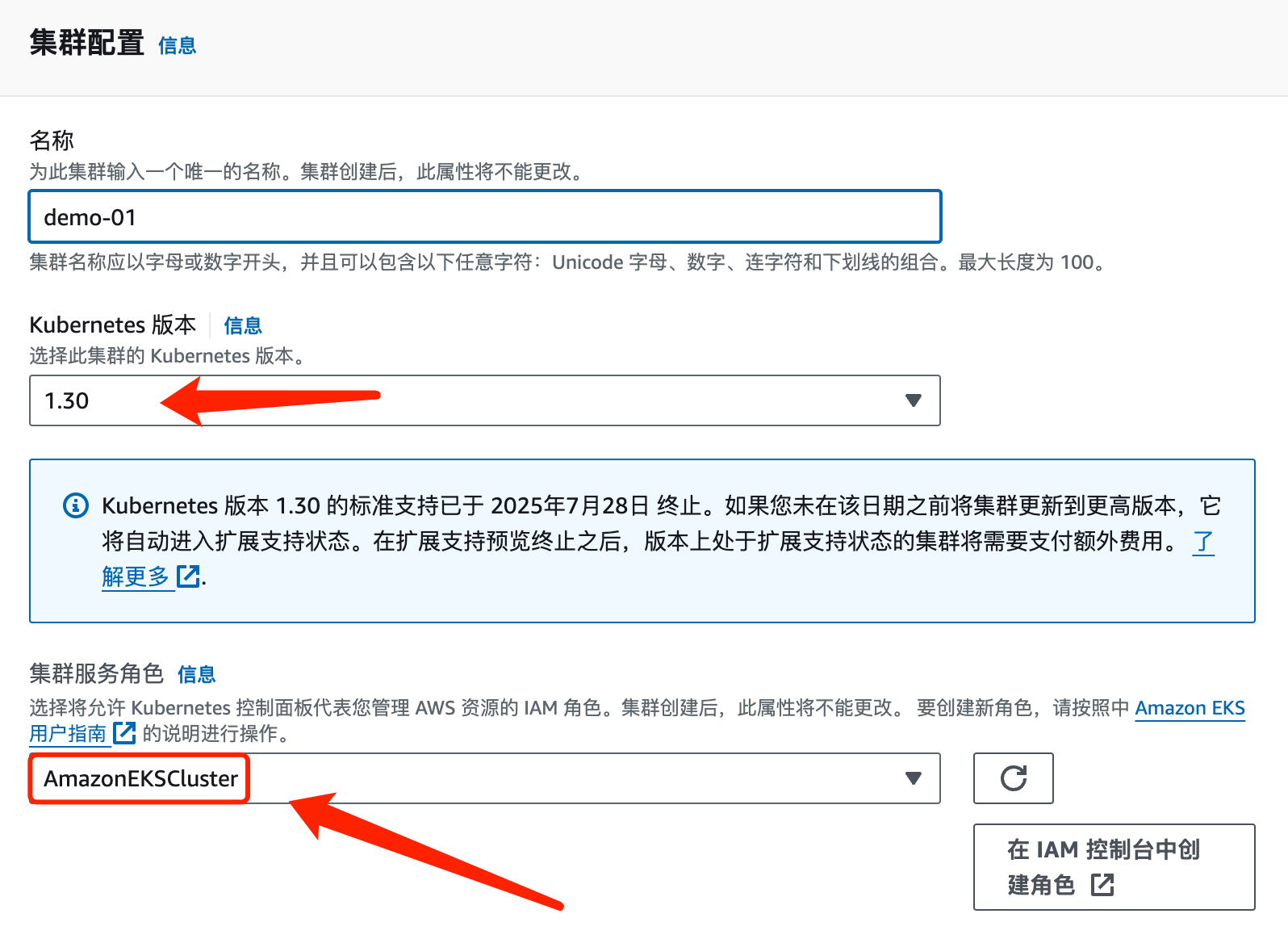
Kubernetes版本直接使用最新版本即可
集群角色选择你所需要的,也可以重新创建新的,这个角色一点要记住
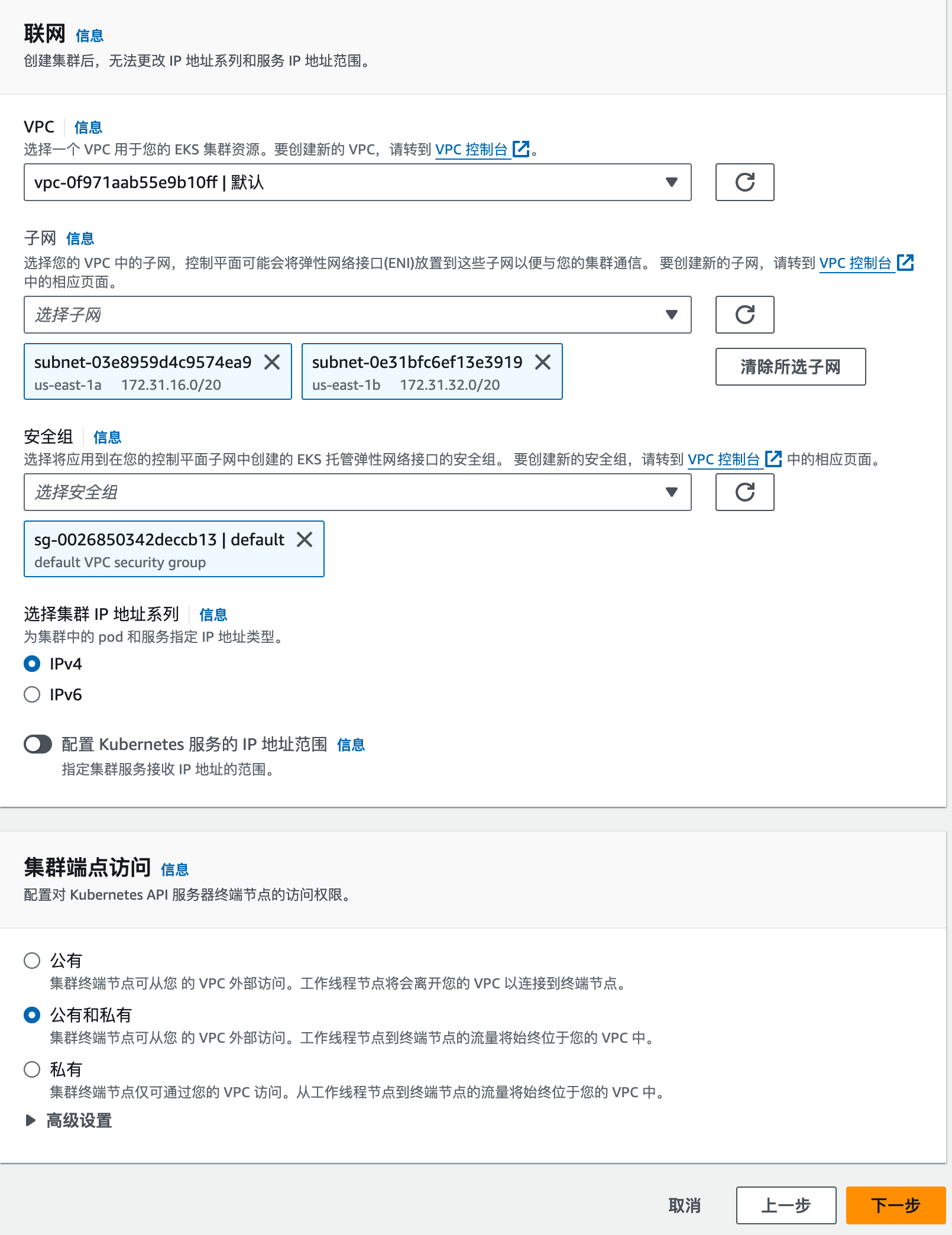
选择新建立的VPC
子网最少选择两个
安全组可以新建一个安全组
其他按照默认即可
这里根据自己的需求选择
插件默认即可
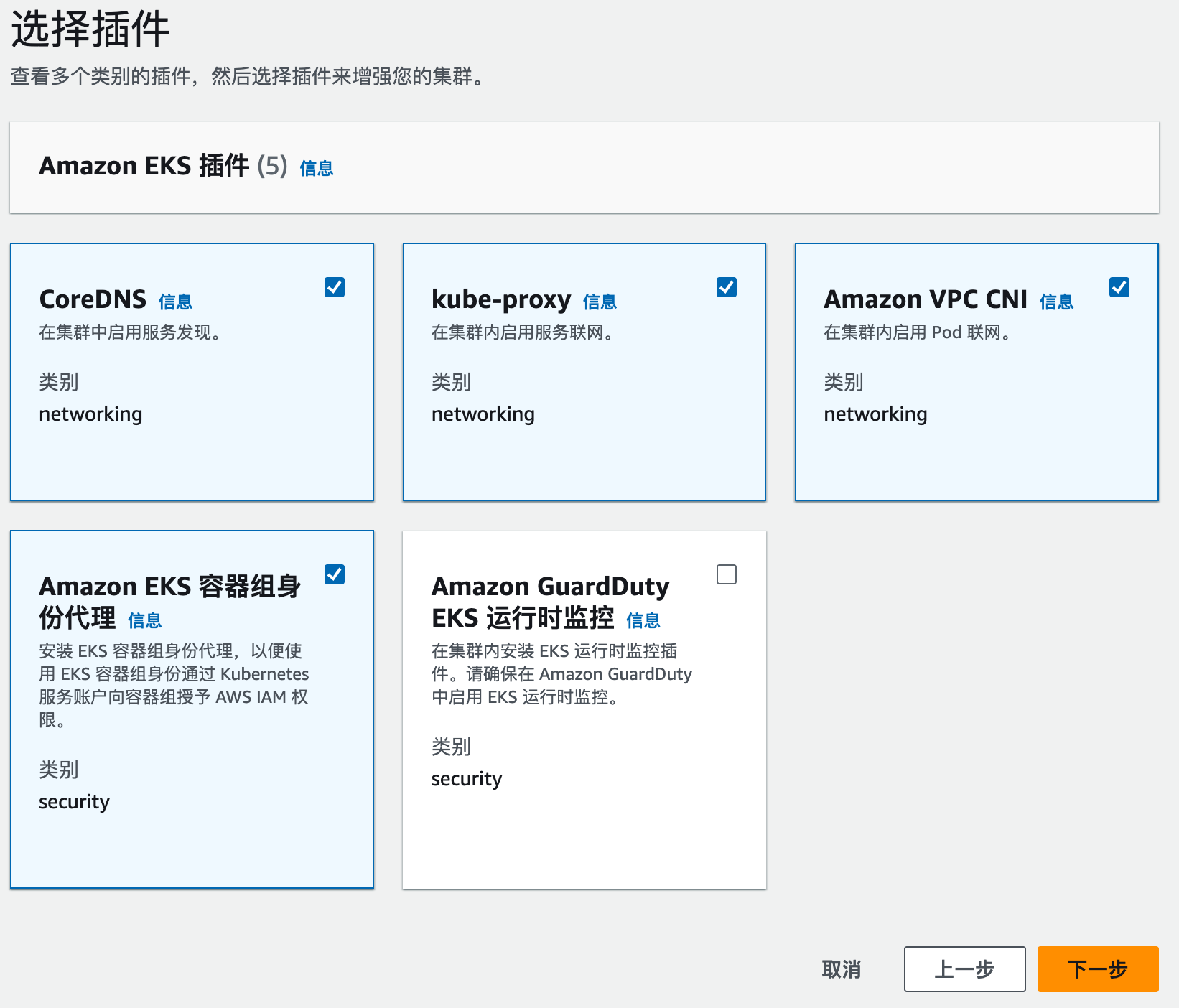
插件版本选择最新的版本即可
最后确定自己的选择好的信息点击创建稍等片刻即可创建成功
2.2 创建控制服务器
如果是线上使用的话可以选择Jenkins服务器或者别的中间件服务器
这里创建一台2核4G50GB的服务器即可
2.3 安装awsctl/eksctl/kubectl
2.3.1 awsctl
https://docs.aws.amazon.com/zh_cn/cli/latest/userguide/getting-started-install.html
sudo yum remove awscli
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/install --bin-dir /usr/local/bin --install-dir /usr/local/aws-cli --update
vim /etc/profile
export PATH="/usr/local/bin/:$PATH"
source /etc/profile
aws --version
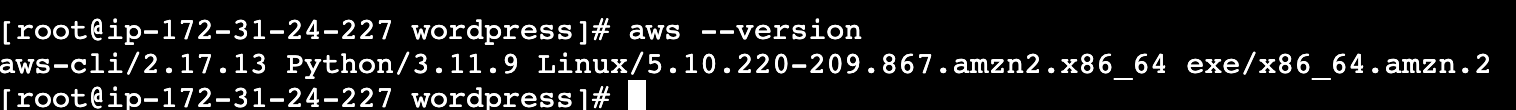
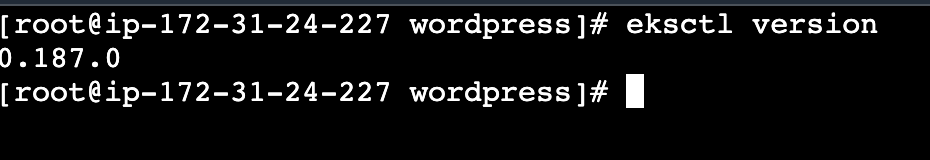
2.3.2 eksctl
curl --silent --location "https://github.com/weaveworks/eksctl/releases/latest/download/eksctl_$(uname -s)_amd64.tar.gz" | tar xz -C /tmp
sudo mv -v /tmp/eksctl /usr/local/bin
eksctl version
2.3.3 kubectl
https://docs.aws.amazon.com/zh_cn/eks/latest/userguide/install-kubectl.html
curl -O https://s3.us-west-2.amazonaws.com/amazon-eks/1.30.0/2024-05-12/bin/linux/amd64/kubectl
chmod +x ./kubectl
mkdir -p $HOME/bin && cp ./kubectl $HOME/bin/kubectl && export PATH=$HOME/bin:$PATH
echo 'export PATH=$HOME/bin:$PATH' >> ~/.bashrc
kubectl version --client
2.4 连接Kubernetes集群
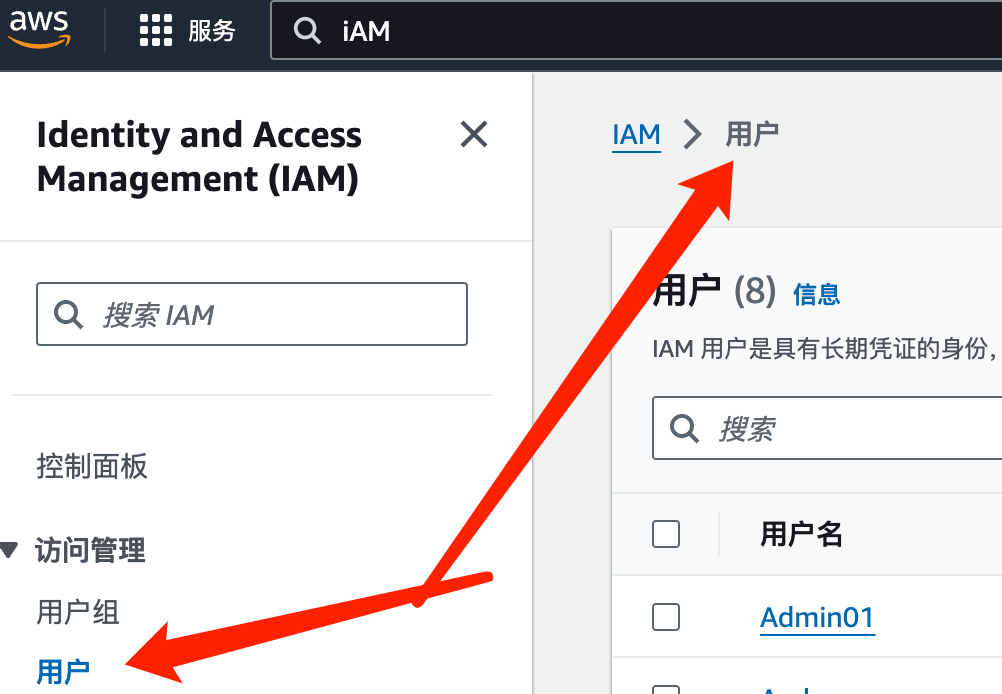
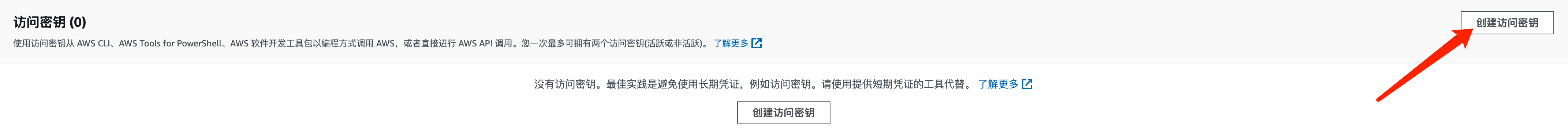
2.4.1 awsctl进行身份验证
export AWS_ACCESS_KEY_ID=AKIAxxxxxxxxxxPLE
export AWS_SECRET_ACCESS_KEY=wxxxxxMI/K7qweqeG/bPqweqweqweqweEY
export AWS_DEFAULT_REGION=us-west-2(Kubernetes集群所在地区)
aws configure
2.4.2 使用kubectl访问我的集群
https://docs.aws.amazon.com/zh_cn/eks/latest/userguide/create-kubeconfig.html
aws eks update-kubeconfig --region region-code --name my-cluster
kubectl get svc
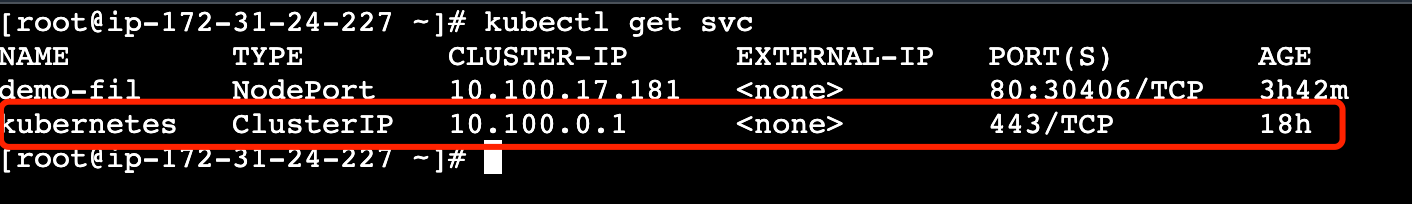
kubectl get nodes
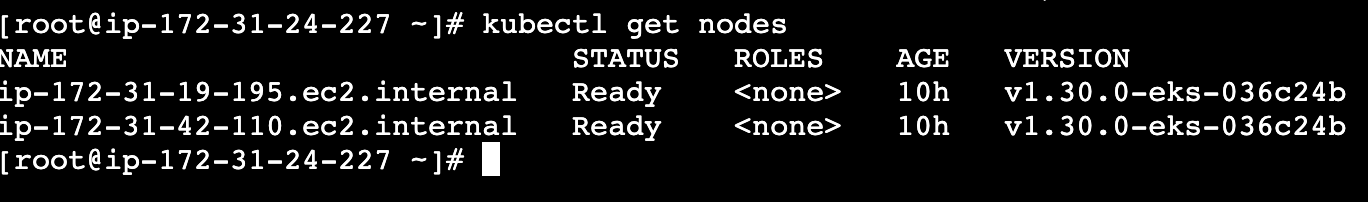
2.5 创建AWS Load Balancer Controller
1.它通过配置应用负载均衡来满足kubernetes的ingress资源.
2.它通过配置网络负载均衡来满足kubernetes的Service资源.
2.5.1 创建策略
https://docs.aws.amazon.com/zh_cn/eks/latest/userguide/lbc-helm.html
cd ~/environment
mkdir -p manifests/alb-ingress-controller && cd manifests/alb-ingress-controller
eksctl utils associate-iam-oidc-provider \
--region ${AWS_REGION} \
--cluster eks-demo-hy \
--approve
aws eks describe-cluster --name eks-demo-hy --query "cluster.identity.oidc.issuer" --output text
aws iam list-open-id-connect-providers | grep <enter the id>
curl -O https://raw.githubusercontent.com/kubernetes-sigs/aws-load-balancer-controller/v2.7.2/docs/install/iam_policy.json
aws iam create-policy \
--policy-name AWSLoadBalancerControllerIAMPolicy \
--policy-document file://iam_policy.json
eksctl create iamserviceaccount \
--cluster=my-cluster \
--namespace=kube-system \
--name=aws-load-balancer-controller \
--role-name AmazonEKSLoadBalancerControllerRole \
--attach-policy-arn=arn:aws:iam::111122223333:policy/AWSLoadBalancerControllerIAMPolicy \
--approve
2.5.2 安装 cert-manager
kubectl apply \
--validate=false \
-f https://github.com/jetstack/cert-manager/releases/download/v1.13.5/cert-manager.yaml
2.5.3 安装AWS Load Balancer Controller
curl -Lo v2_7_2_full.yaml https://github.com/kubernetes-sigs/aws-load-balancer-controller/releases/download/v2.7.2/v2_7_2_full.yaml
sed -i.bak -e 's|your-cluster-name|my-cluster|' ./v2_7_2_full.yaml
kubectl apply -f v2_7_2_full.yaml
curl -Lo v2_7_2_ingclass.yaml https://github.com/kubernetes-sigs/aws-load-balancer-controller/releases/download/v2.7.2/v2_7_2_ingclass.yaml
kubectl apply -f v2_7_2_ingclass.yaml
kubectl get deployment -n kube-system aws-load-balancer-controller

3.部署服务测试EKS集群可用性
3.1 部署WordPress
apiVersion: apps/v1
kind: Deployment
metadata:
name: demo-fil
namespace: default
spec:
replicas: 3
selector:
matchLabels:
app: demo-fil
template:
metadata:
labels:
app: demo-fil
spec:
containers:
- name: demo-fil
image: wordpress:latest
imagePullPolicy: Always
ports:
- containerPort: 80
apiVersion: v1
kind: Service
metadata:
name: demo-fil
annotations:
alb.ingress.kubernetes.io/healthcheck-path: "/"
spec:
selector:
app: demo-fil
type: NodePort
sessionAffinity: None
externalTrafficPolicy: Cluster
ports:
- protocol: TCP
port: 80
targetPort: 80
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: "demo-ingress"
namespace: default
annotations:
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/target-type: ip
alb.ingress.kubernetes.io/subnets: subnet-xxxxxyyyy,subnet-xxxxxyyy
nginx.ingress.kubernetes.io/whitelist-source-range: '0.0.0.0/0'
spec:
ingressClassName: alb
rules:
- http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: "demo-fil"
port:
number: 80
kubectl apply -f word-depl.yaml
kubectl apply -f word-svc.yaml
kubectl apply -f word-ing.yaml
kubectl logs -n kube-system deployment.apps/aws-load-balancer-controller
3.2 查看是否创建成功
kubectl get all -n default -o wide
kubectl get ing -n default -o wide
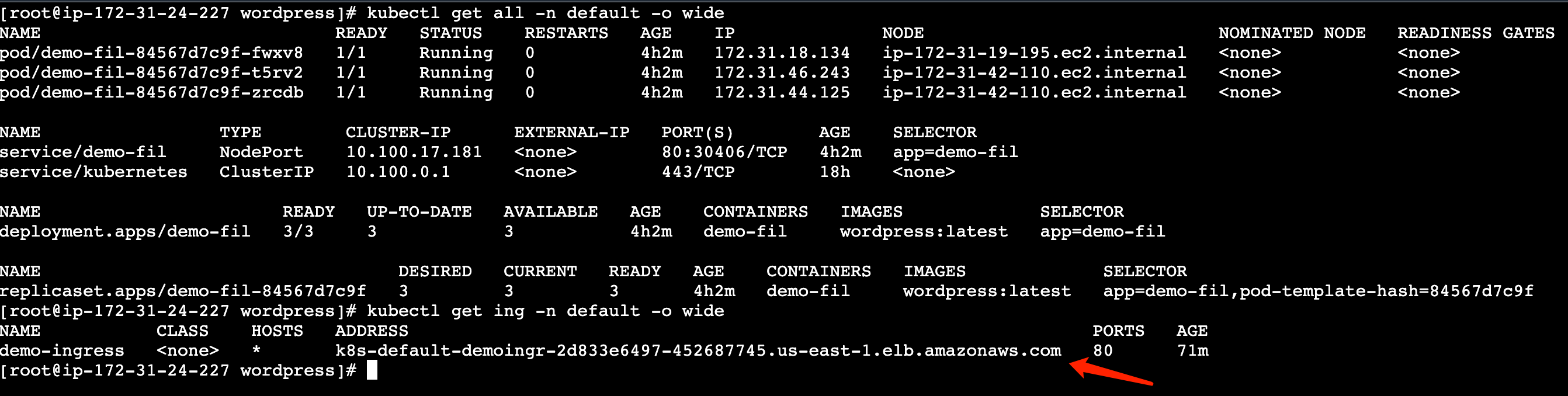
此处ingress提示ELB已经创建成功.
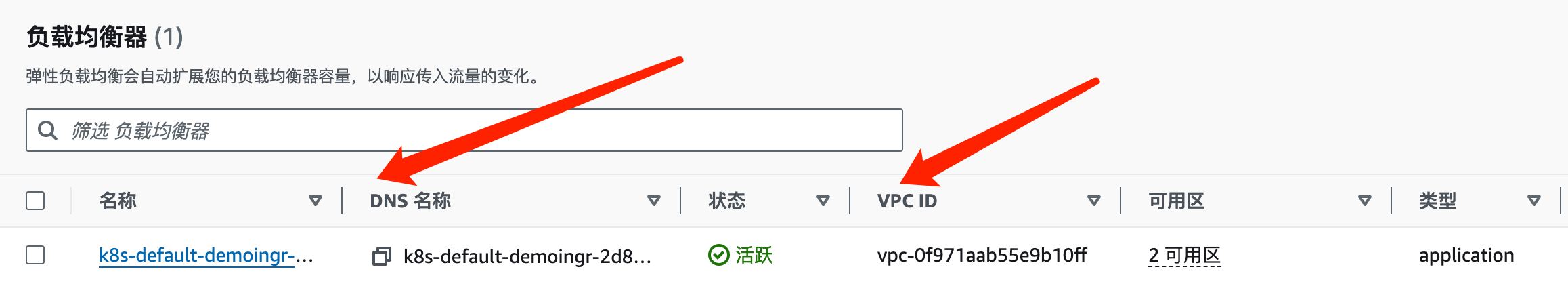
4.踩坑
4.1 EKS集群子网添加标签
搜索 ---> VPC ---> 子网 ---> (你当时创建EKS集群时选择的子网)
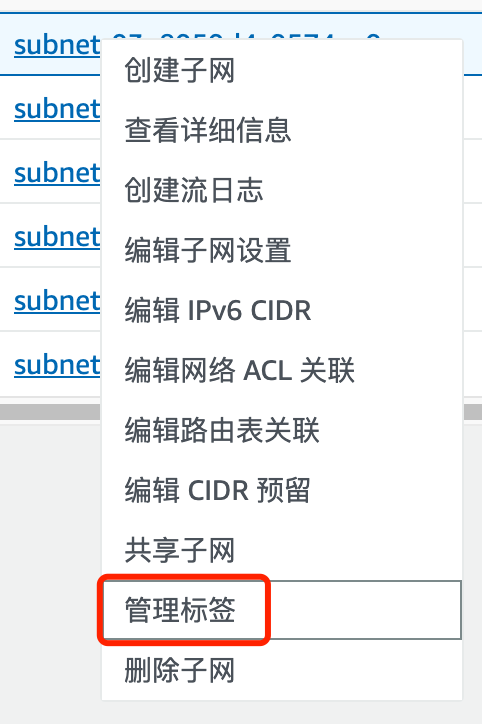
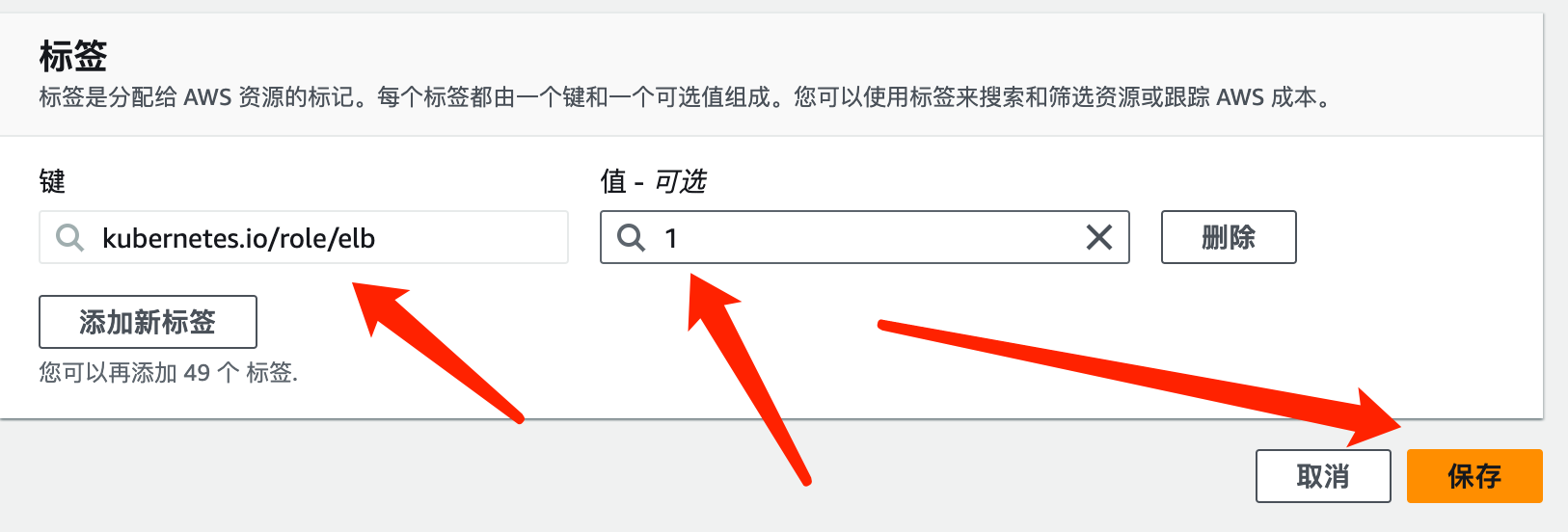
kubernetes.io/role/elb
1
kubernetes.io/role/internal-elb
1
4.2 Ec2CallAWS角色添加AllowELBOperations策略
AllowELBOperations
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:AddTags",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:CreateTargetGroup",
"elasticloadbalancing:ModifyTargetGroup",
"elasticloadbalancing:DeleteTargetGroup"
],
"Resource": "*"
}
]
}
4.3 Ingress(内网)
annotations:
kubernetes.io/ingress.class: "alb"
alb.ingress.kubernetes.io/scheme: "internal"
alb.ingress.kubernetes.io/subnets: "subnet-xxxxxx,subnet-yyyyyy"





















评论区